15 phishing email examples including real-life cases
15 documented phishing attacks show how fraudsters exploit email-dependent verification to steal client funds. Learn the red flags that protect your business from the next attack.
Tyler Adams
8 minutes
Scams
Jul 19, 2021
Oct 3, 2025
Phishing remains the #1 entry point for real estate wire fraud. According to CertifID's 2025 State of Wire Fraud report, nearly $500 million in annual losses stem from business email compromise attacks targeting the real estate industry.
This article examines 15 real phishing examples, reveals the red flags you must recognize, and demonstrates how removing email from money movement becomes the only reliable defense against increasingly clever attackers.
What is a phishing email?
Phishing emails are fraudulent messages designed to impersonate trusted parties and manipulate recipients into revealing sensitive information or authorizing financial transactions.
In real estate, attackers commonly pose as lenders, underwriters, sellers, or even your own clients to redirect funds or capture wire instructions.
Consider a typical mortgage payoff fraud: You receive what appears to be a legitimate email from Mr. Cooper, complete with proper branding and formatting, requesting updated payoff information for a closing scheduled tomorrow.
The sender's address looks authentic, the urgency feels reasonable, and the request seems routine—until you discover that $275,000 has been wired to a fraudulent account.
These attacks work because they prey on the trust and time pressure built into real estate transactions.
If this feels uncomfortably plausible, you’re right. In the video below, CertifID’s Tom Cronkright and Kimberly Casanova show how fraudsters use ‘routine’ callbacks in real payoff fraud and what to do instead.
How phishing emails work (and why they bypass gut checks)
Phishing attacks succeed through social engineering—the psychological manipulation of human trust and decision-making under pressure. Fraudsters understand that title professionals work in high-stress environments where quick responses often keep a closing on track.
The mechanics involve techniques like:
- Compromised email accounts that provide authentic communication histories,
- Lookalike domains that differ by a single character
- Carefully researched transaction details gathered from public records.
Modern attackers use AI to study email patterns and generate messages that look and read like the real thing.
The problem with manual verification becomes clear during peak closing periods. When your team processes hundreds of files monthly, the callback-and-verify approach breaks down.
Checking emails on mobile devices after hours, pressure to respond quickly to "urgent" requests, and sheer volume make it easier for sophisticated fakes to slip through.
Types of phishing emails include:
- Classic phishing: mass emails with generic language and low-quality branding
- Spear phishing: highly targeted emails with personal details or transaction information
- Business email compromise (BEC): attackers impersonate trusted contacts by compromising real accounts
- CEO fraud: scammers pose as executives pressuring urgent actions (often leading to business email compromise)
- Brand impersonation: fake messages mimicking PayPal, Microsoft, Google, or DocuSign
- Government/tax scams — fraudulent IRS or regulatory messages demanding payments
- Smishing and vishing: phishing by text or phone call instead of email
Why real estate is a prime target
Real estate has a perfect storm for fraud: large transaction amounts, multiple parties communicating across fragmented systems, and historically low cybersecurity infrastructure.
With the U.S. median home sale price in Q2 2025 reaching $410,800, each successful attack yields hundreds of thousands of dollars.
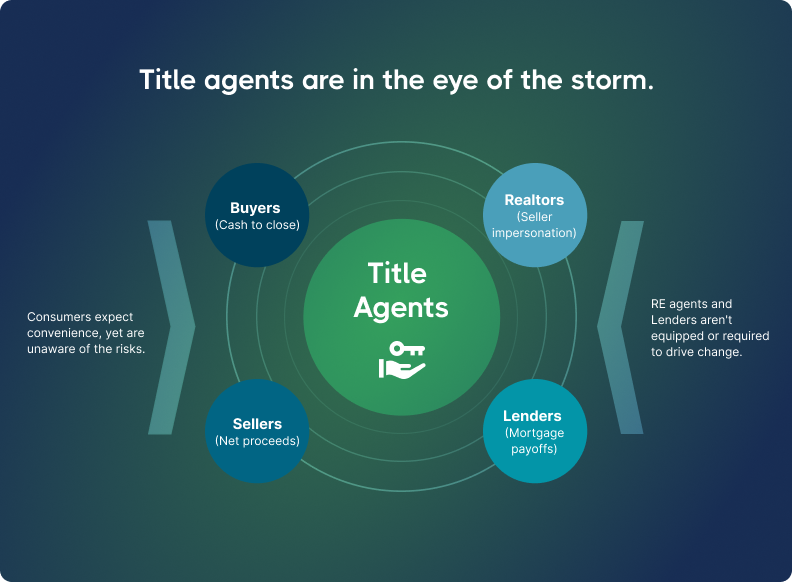
The industry's vulnerability stems from its decentralized nature. Unlike banking, which invested heavily in cybersecurity following decades of attacks, real estate relies on thousands of independent title companies and law firms with varying security sophistication. State-by-state regulation creates inconsistent standards.
Title companies and closing attorneys still rely on email for critical tasks like verifying mortgage payoffs, confirming seller identities, and sending buyer wire instructions.
Attorneys and clients keep using email because it feels familiar, but that dependence gives fraudsters more chances to slip in and divert funds.
CertifID's analysis shows that once a company experiences a single high-risk transaction flag, the rate of suspicious activity increases up to 6x compared to peer firms. This suggests organized criminal groups systematically target specific businesses, hoping to exploit process gaps during busy closings.
Why email-dependent wire verification puts your business at risk
Every inbox functions as an unregulated payment rail, capable of authorizing hundreds of thousands of dollars in wire transfers without meaningful verification. Unlike banking systems with multi-factor authentication and fraud monitoring, email offers no safeguards to verify senders or wire instructions.
A single successful attack can wipe out your annual technology budget and threaten your business's survival. Traditional insurance policies often exclude wire fraud losses, leaving you personally liable for client funds.
The regulatory landscape adds another risk layer. As wire fraud incidents increase, state bar associations and insurance carriers scrutinize firms' cybersecurity practices more closely, potentially imposing higher premiums, coverage exclusions, or regulatory sanctions.
Phishing email examples
1. Dropbox phishing email example
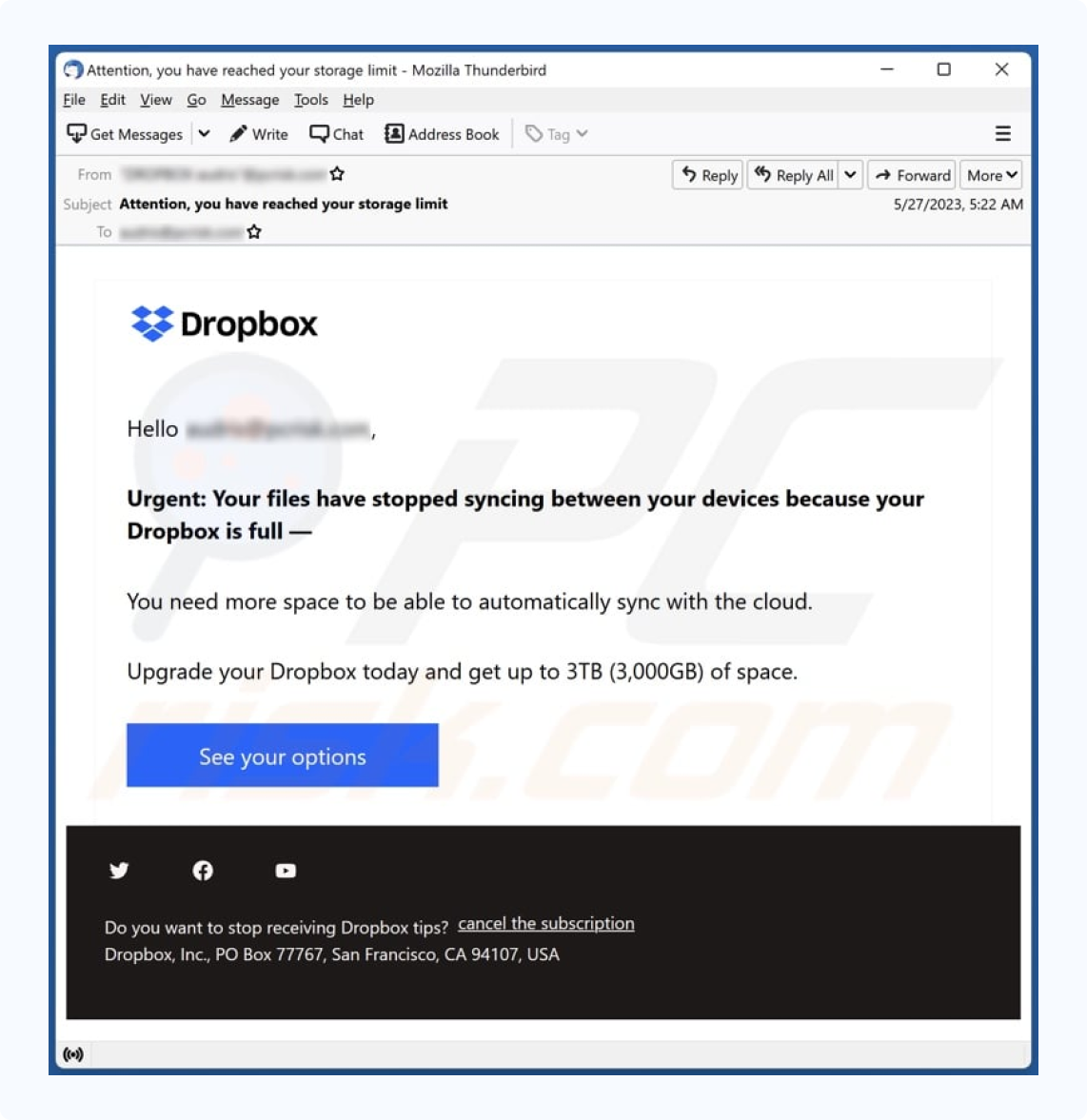
Document-sharing platforms like Dropbox, Google Docs, and DocuSign are common targets in real estate transactions. These phishing emails are sent from generic-sounding names or compromised accounts of people you know. If a contact’s account was hacked, their email list can be used to spread the scam.
Clicking the link takes you to a fake login page that captures credentials while appearing nearly identical to the real Dropbox interface.
Red flags:
- URL contains "dropbox" but isn't a Dropbox domain
- Login page offers multiple email provider options
- Error message claims "Dropbox is having difficulties" before redirecting to the real site
2. Google Docs phishing email example
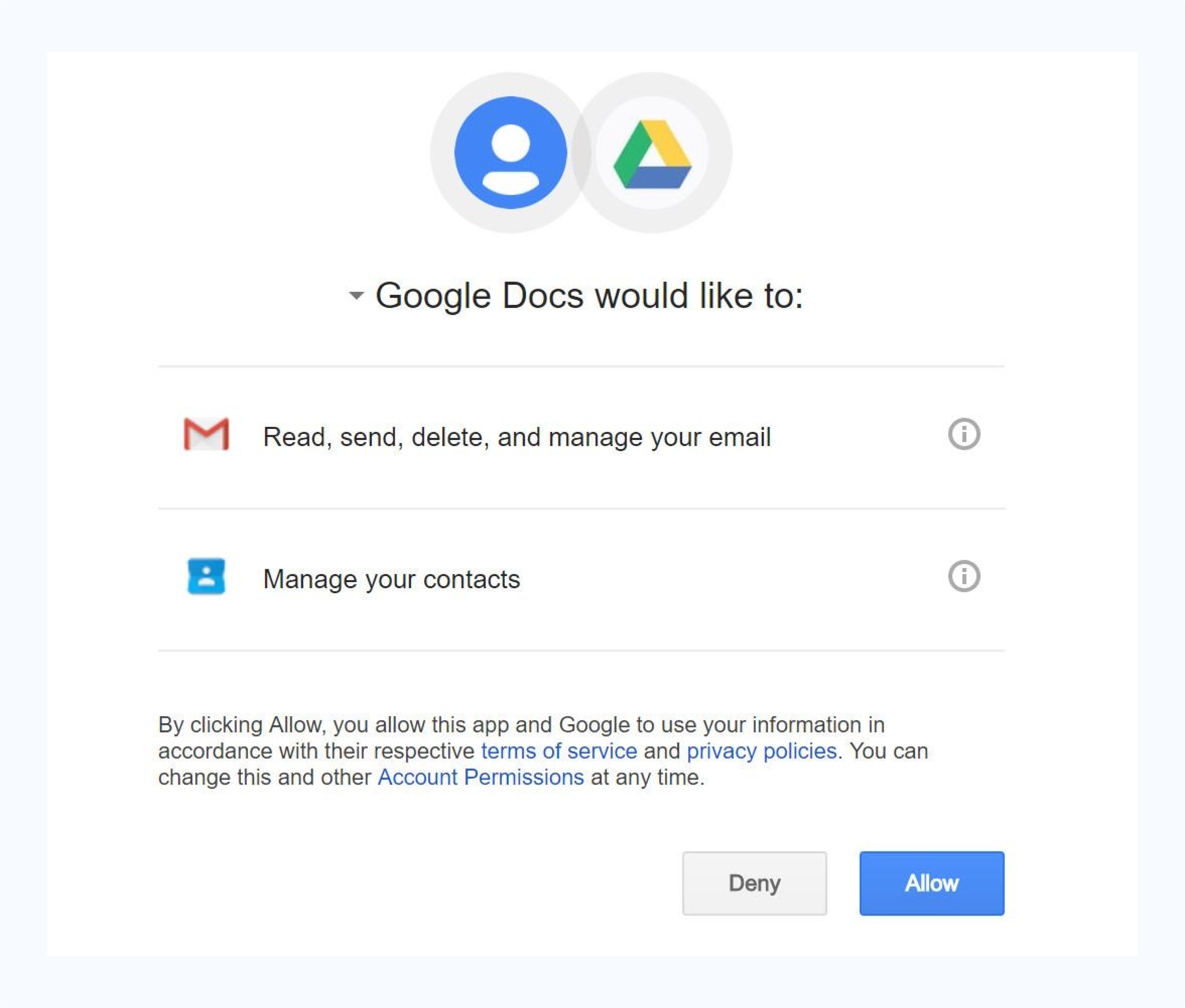
Like the Dropbox scam, this one starts with an email supposedly from someone you know.
Unlike the Dropbox scam, however, clicking on the link takes you to a real Google Docs page, and asks the user to grant permission to a third-party application entitled “Google Docs,” despite the fact it is not associated with the platform
Google has since added stricter rules for third-party apps, including restrictions on what names they can use.
If you grant access, fraudsters can use your login credentials to obtain your personal information, including your contacts list, to spread the attack.
Red flags:
- Hard to spot, but if you click the developer information, you can see it is not from the user you thought it was, after all
3. DocuSign phishing email example
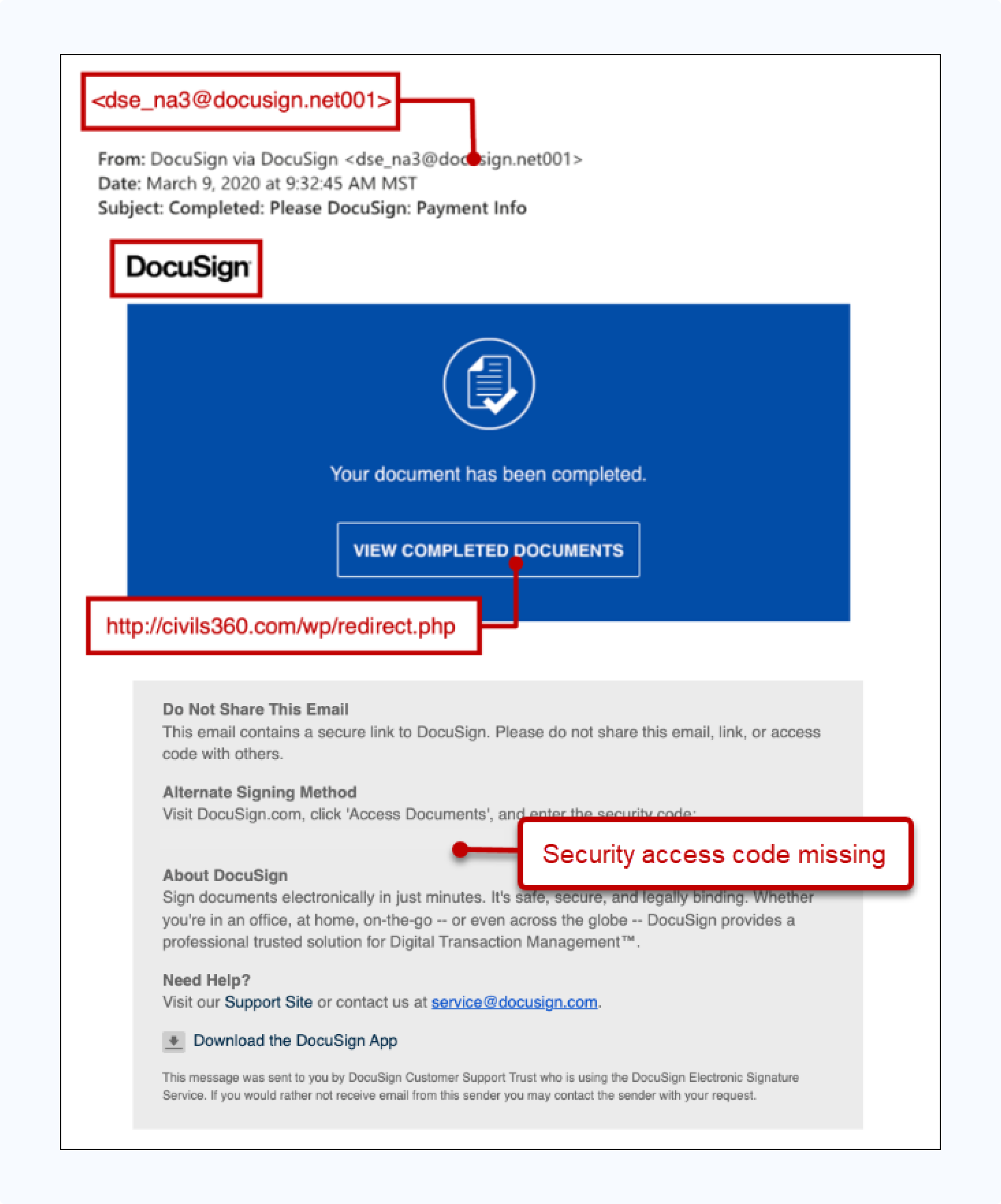
The DocuSign phishing email mimics the company’s document completion notifications. They often claim "Your document has been completed" and use authentic branding, logos, and the familar blue color scheme.
The email comes from a suspicious sender address, and clicking the "VIEW COMPLETED DOCUMENTS" button redirects you to a malicious domain instead of DocuSign's official servers.
The attack works because people trust DocuSign notifications, particularly in real estate transactions where document signing is routine.
Legitimate DocuSign emails always include a 32-character security code in the "Alternate Signing Method" section. Phishing emails leave this out.
Red flags:
- Missing security access code in the alternate signing method section
- "View Completed Documents" button links to external, non-DocuSign domain
- Sender domain contains extra characters ("net001") not used by legitimate DocuSign emails
4. Bank of America phishing email example
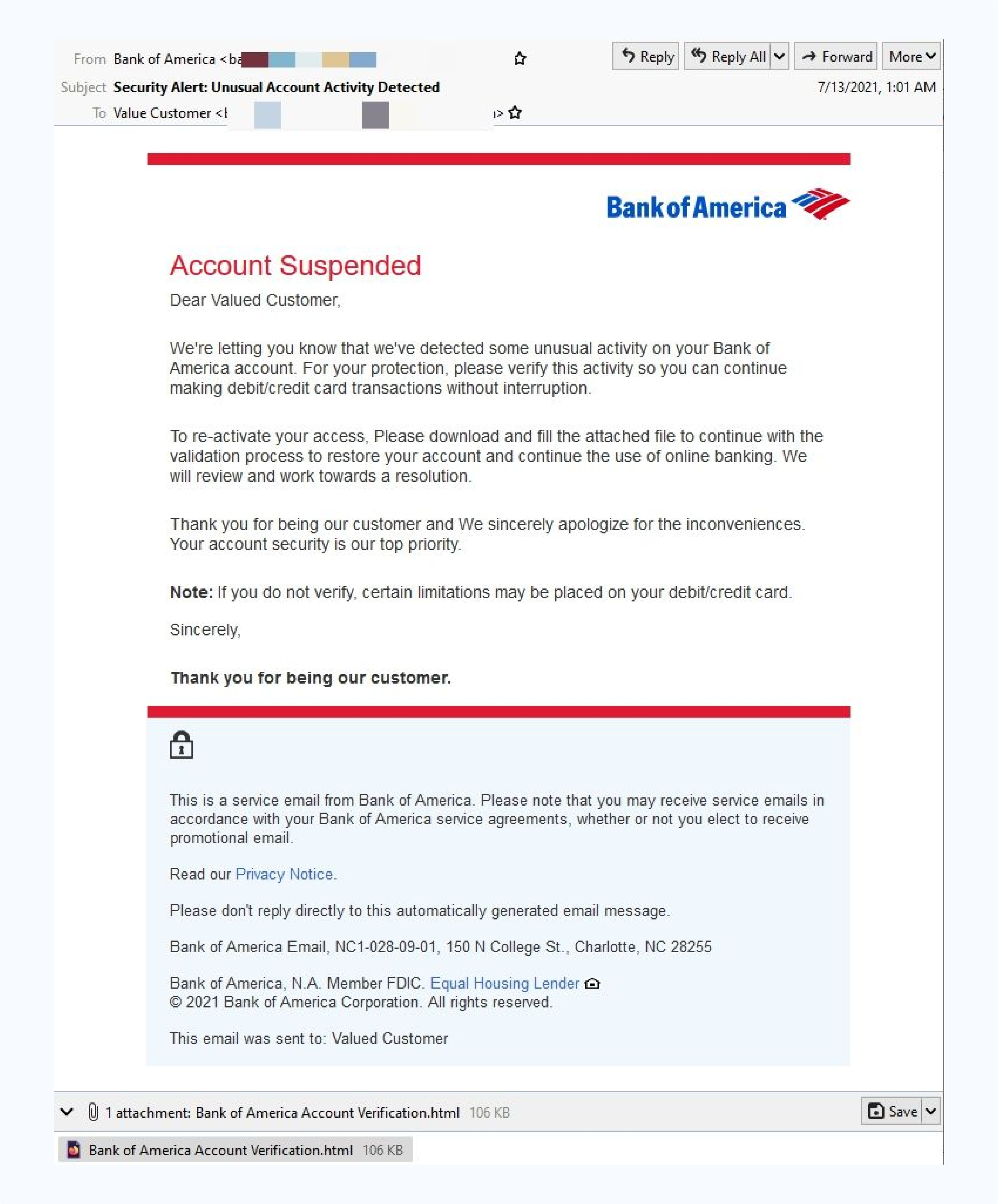
A Bank of America phishing email uses authentic branding to claim an account has been suspended due to "unusual activity detected."
The email creates urgency by threatening account limitations unless the recipient downloads an HTML attachment for "verification." The message looks professional with clean formatting, footer disclaimers, and contact details that appear legitimate.
However, legitimate banks never ask customers to download attachments to verify their accounts. The email uses a generic greeting like "Valued Customer" and try to pressure the reader with threats debit or credit card limitations.
The email’s polished appearance makes it harder to detect, especially for title professionals juggling multiple business banking relationships.
Red flags:
- HTML attachment required for "verification"
- Generic greeting "Valued Customer" instead of account holder's name
- Urgent threats of account limitations to pressure immediate action
- Requests to download files rather than directing to official bank portals
5. Wells Fargo phishing email example

Wells Fargo phishing emails mimic the bank’s red and yellow branding and warn that an account has been locked pending verification. The email claims purchases and balance transfers will be declined, creating urgency around frozen access.
It directs recipients to what looks like the correct URL to unlock their account. The email’s professional formatting makes the request appear credible.
However, the sender domain differs from Wells Fargo’s official wellsfargo.com; in this case it’s noreply@weiis-mail.com. Phishing domains commonly add hyphens, swap letters, or insert extra words to mimic a real address.
These tactics can bypass email security filters and exploit recipients’ unfamiliarity with text-based phishing. Wells Online is also not a legitimate name used by Wells Fargo.
Red flags:
- Sender domain "weiis-mail.com" instead of official "wellsfargo.com"
- Urgent account lockdown claims designed to provoke immediate action
- Generic verification URL that doesn't match legitimate Wells Fargo domains
- Unsolicited account status notifications
6. PayPal phishing email example
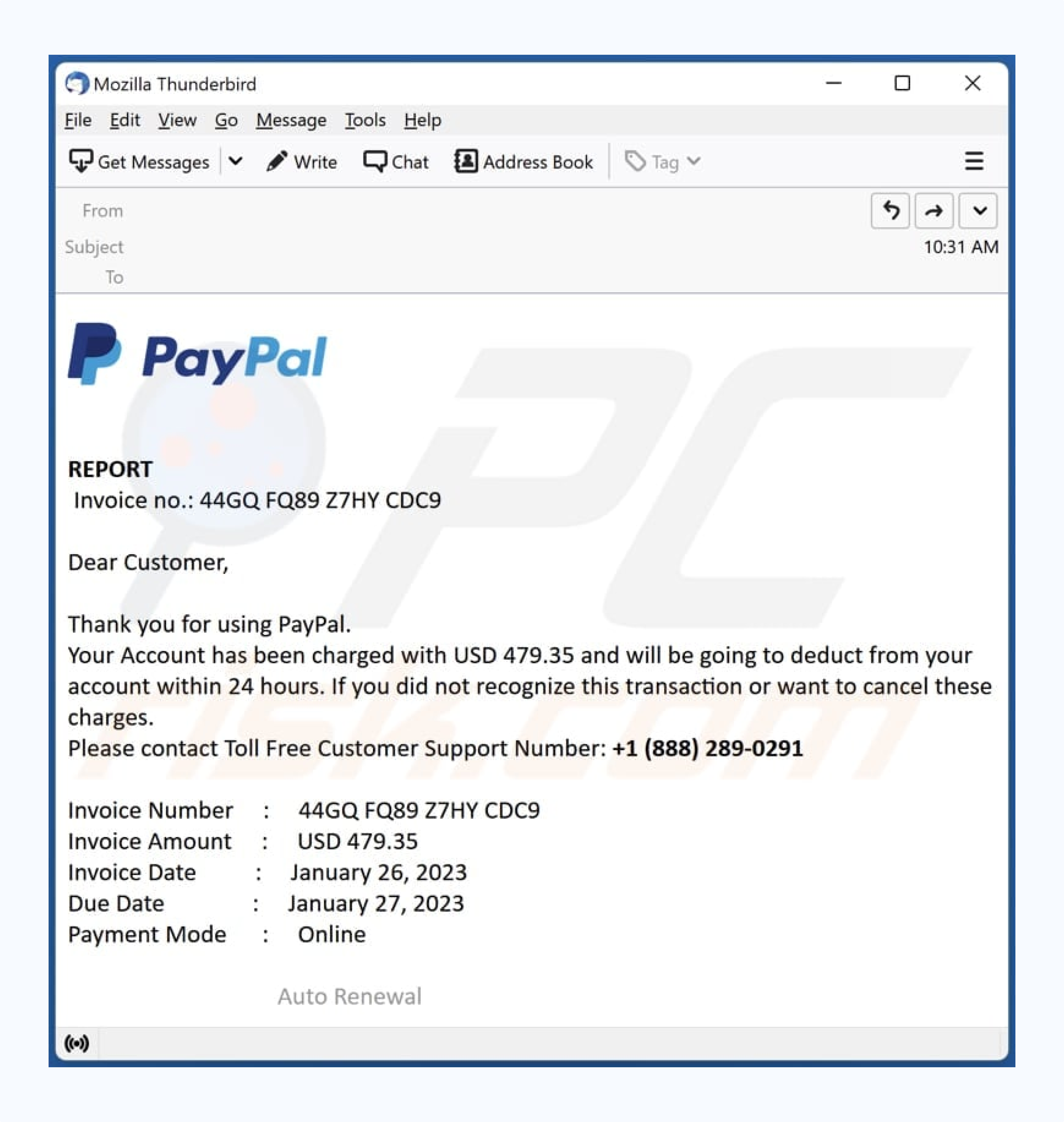
This PayPal phishing example uses the company’s blue branding to announce that an unexpected $479.35 charge will be deducted from the recipient's account.
The email creates panic by claiming unauthorized charges while providing a toll-free support number for "cancellation." It includes convincing details like invoice numbers and dates.
However, the message uses generic salutation "Dear Customer" and asks you to call a phone number rather than directing users to PayPal's official website, which legitimate PayPal notifications always do.
Red flags:
- Grammatical errors like "will be going to be deducted”
- Unexpected charge notifications for services you didn't purchase
- Generic greeting "Dear Customer" instead of account holder's name
- Phone number provided for dispute resolution instead of website links
- Urgent 24-hour deadline designed to provoke panic response
7. Email providers phishing example
The same tactics used in document and bank phishing can also target your email credentials, which can give scammers access to the person’s contacts—and, potentially, their banking, shopping, or social media accounts.
Various forms of “validate your account” Gmail messages have made their rounds, telling users to verify their information to avoid account suspension.
They are taken to a real-looking log-in screen, and scammers use their information to access, among other things, the user’s contact list and spread malware or more validation emails.
Users should take note of the URL—which is not actually a Google one—and the fact that, once they’ve entered their email address, their profile picture does not appear before they’re asked for their password.
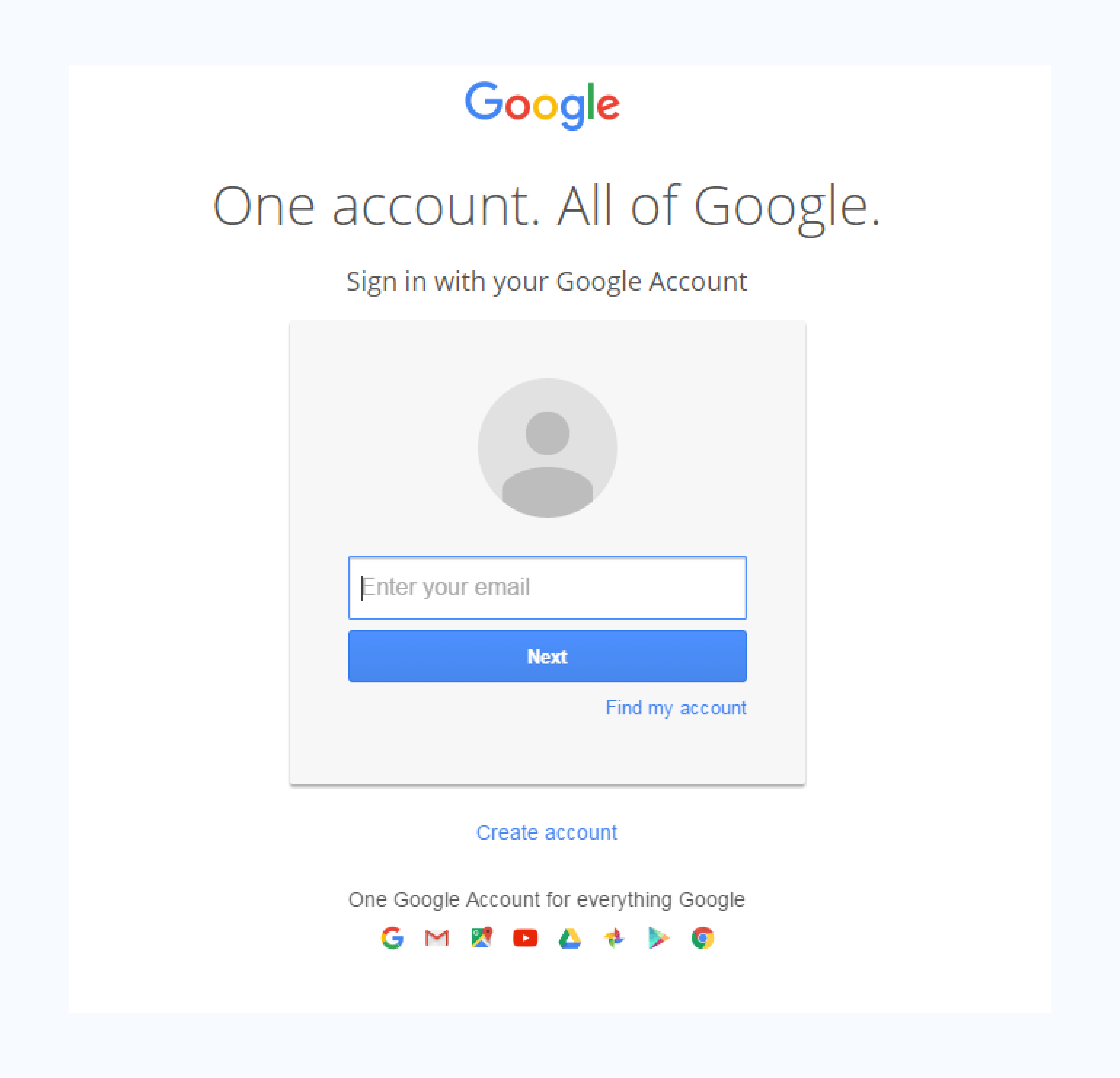
Email provider phishing scams are especially troubling for real estate agents. Many agents still use personal Google email accounts to communicate with clients, even though experts and brokerages advise against it.
A scammer can simply find their email on a real estate site, Facebook, or LinkedIn, and tailor an attack based on that information. From there, they can steal client details and possibly trick them into sending money or banking credentials, all while pretending to be the agent.
8. Real estate phishing email example
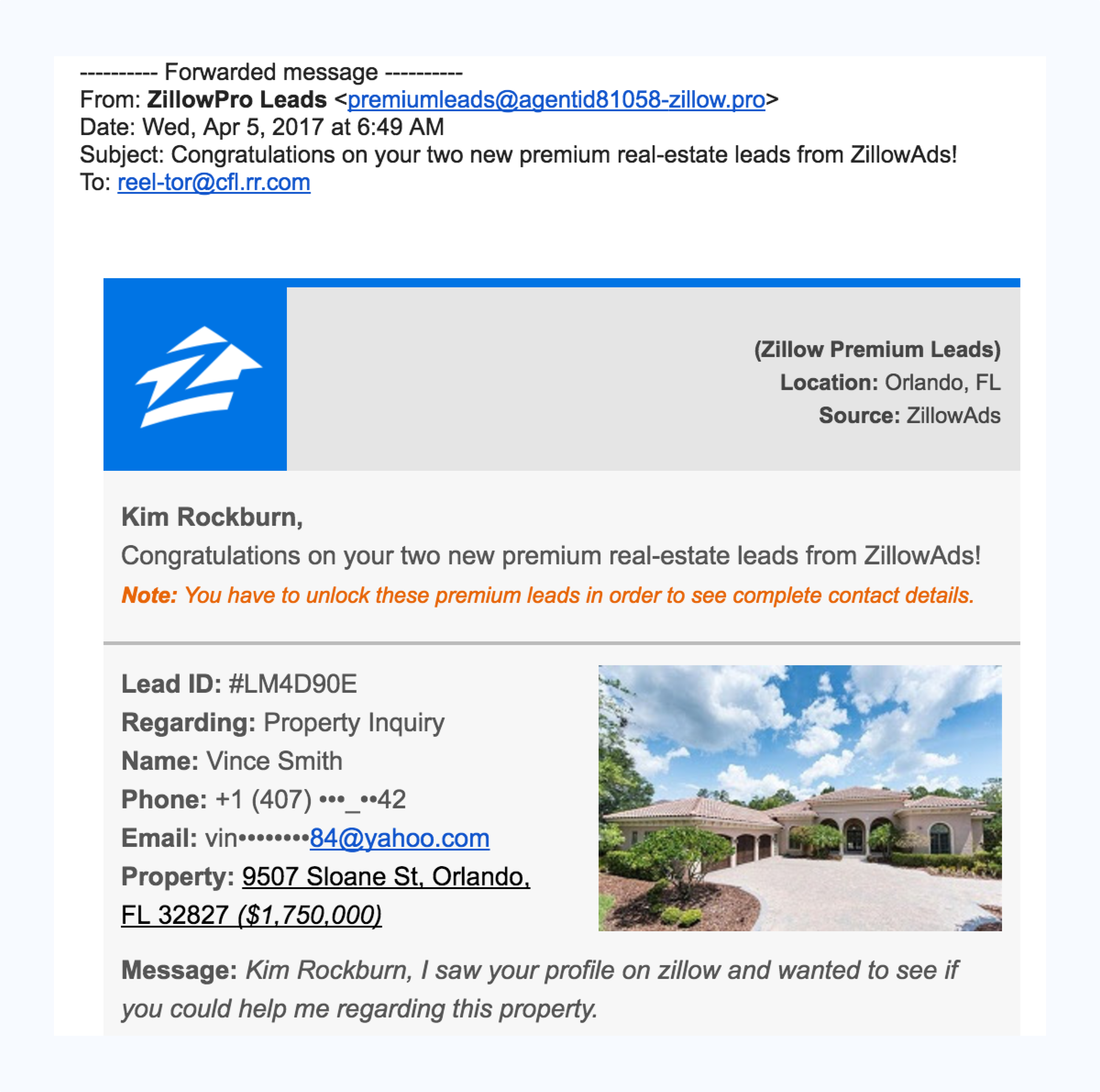
A recent Zillow-based scam was sent to real estate agents, complete with authentic-looking logos, and congratulated the user on their new leads from ZillowAds, which had to be “unlocked” with their contact details and a fee of $5.00.
At least one agent was tricked into providing their credit card information, and missed the only potentially obvious red flag: the fact the domain name was “Zillow.pro” instead of a .com address.
9. Virus and malware phishing example
Virus and malware attacks appear to come from an internal administrator sending an "Important - Internal ONLY" message with a ZIP file attachment (e.g., internal_04531572.zip).
The email is professionally formatted with confidentiality notices, legal copyright information, and detailed file validity data to appear legitimate. The extensive boilerplate text about intellectual property rights and legal consequences creates an illusion of authenticity.
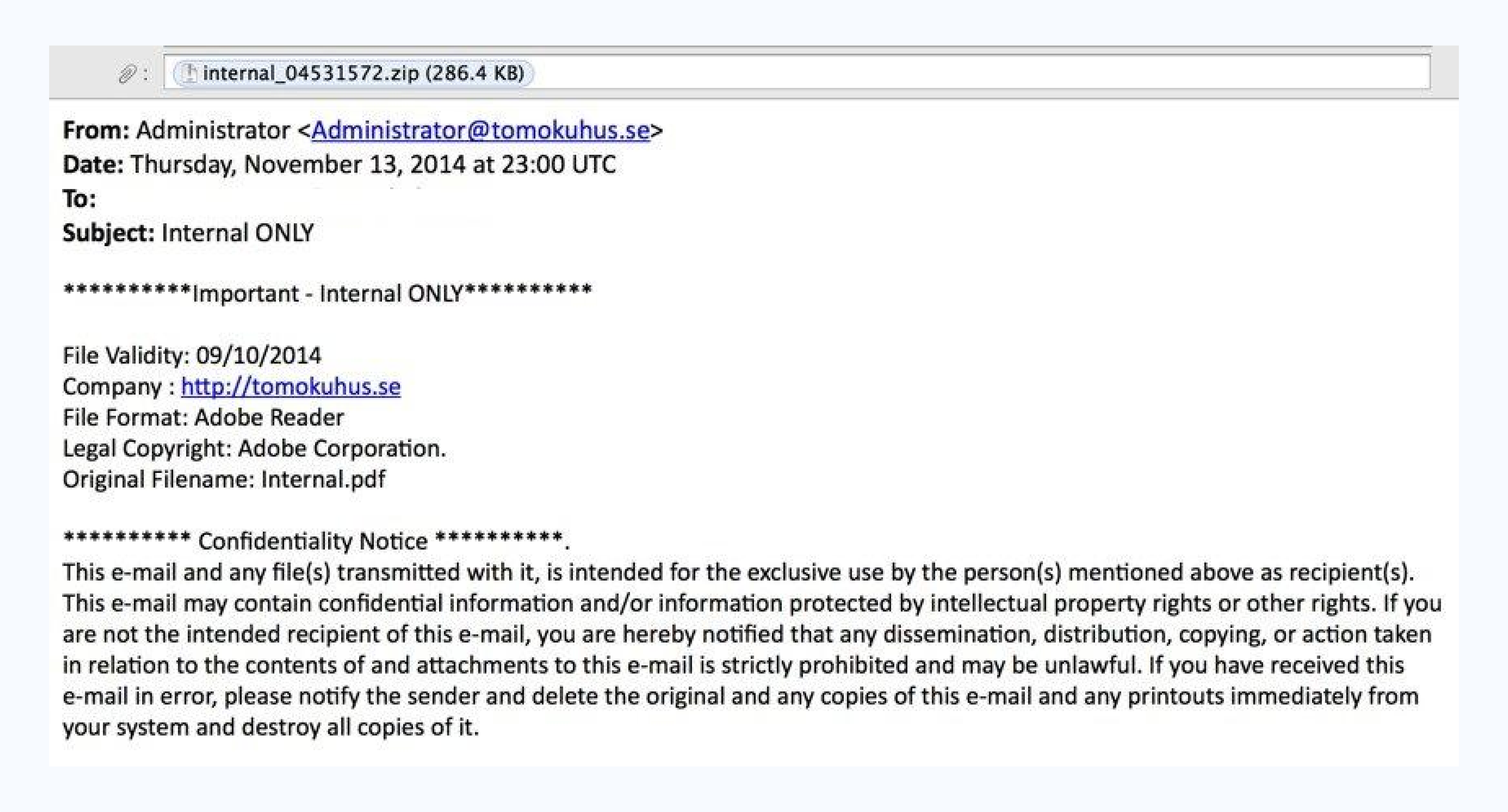
However, the ZIP attachment contains malware that encrypts across your computer once downloaded. The sender's domain, "tomokuhus.se," doesn't match typical internal company addresses, and legitimate internal communications rarely require downloading compressed files for routine business.
10. Facebook phishing email example
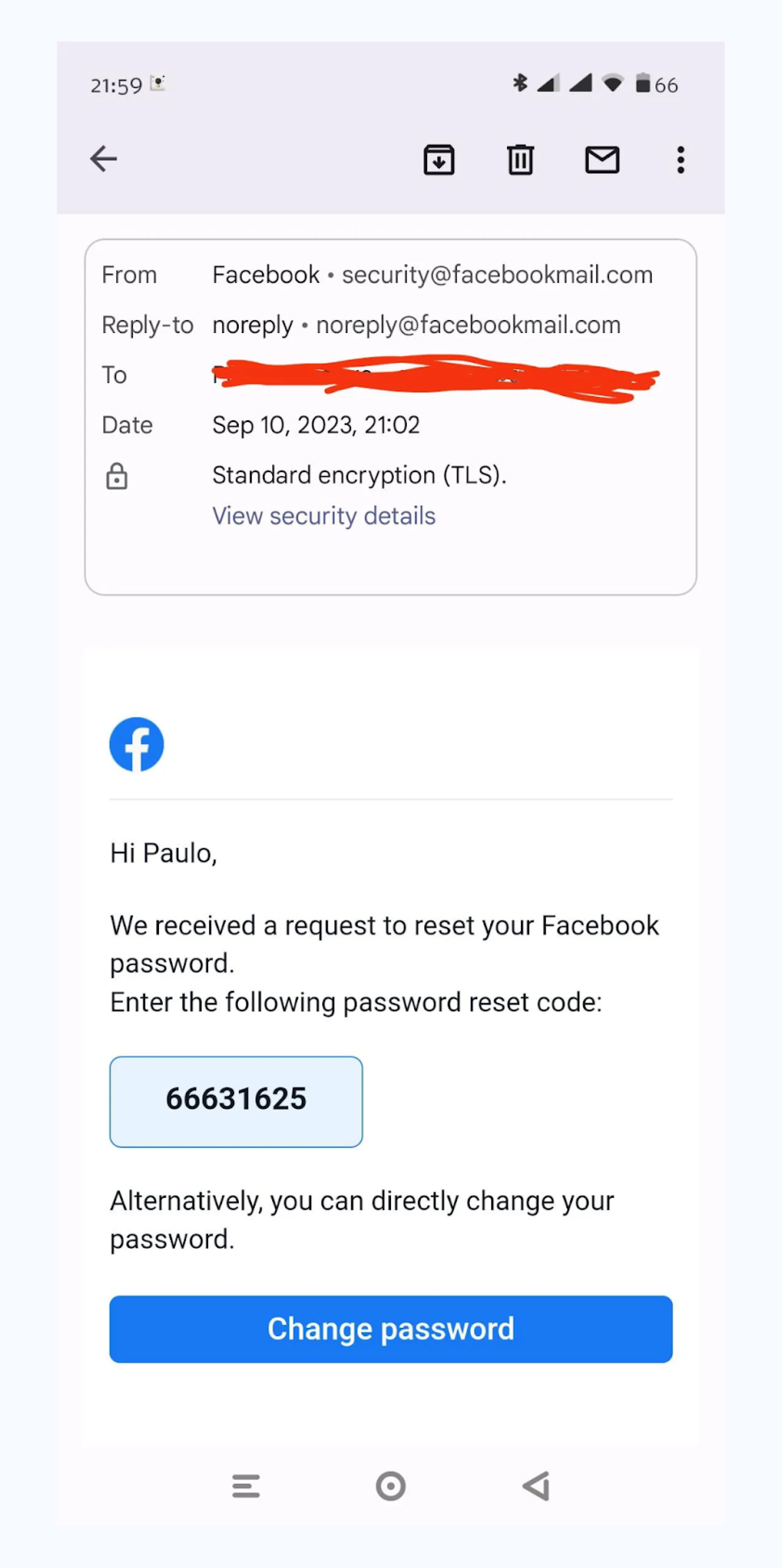
This Facebook phishing email mimics the platform’s branding, uses a personalized greeting "Hi Paulo.", This may come from a look-alike address such as "security@facebookmail.com" and include a reset code (66631625) and "Change password" button to complete the illusion.
Red flags:
- Sender domain "facebookmail.com" instead of official "facebook.com"
- Unsolicited password reset requests you didn't initiate
- Direct reset codes provided in email rather than secure website prompts
- Professional appearance designed to bypass suspicion during mobile viewing
11. Xfinity phishing email example

Attackers send users an email with the Xfinity logo and layout. This message claims to be a confirmation to verify you’ve authorized a payment on a credit card.
Since it’s a fake number, it confuses the target and entices them to click on the “Comcast Billing Invoice” link in the hopes of understanding or fixing the error.
This link leads to a fake domain that prompts the user to download a .php file they believe to be the invoice. Instead, it contains a virus that infects your computer. This malware can compromise secure information stored therein.
Red flags:
- Does not use the customer's name or account number
- Link in the email. Genuine providers direct customers to the company’s official website, which always requires logging in
12. Amazon phishing email example

Amazon phishing emails like this use Amazon's branding and warn, "We have locked your Amazon account and all pending orders," citing billing information mismatches. The email creates urgency by threatening order cancellation within 3 days unless the recipient clicks "Check Now" to verify billing details.
Red flags:
- Displays as mailing list rather than official Amazon communication
- Generic greeting "Greetings from Amazon" instead of account holder's name
- Urgent 3-day deadline designed to provoke immediate panic
- Requests verification through external "Check Now" button
13. Inheritance scam email example

This inheritance scam email uses formal letterhead formatting to announce a £32 million inheritance opportunity from a deceased Libyan national.
The scammer poses as "Mr. Jerry Smith," a bank auditor who discovered an abandoned account, offering 35% of funds in exchange for serving as "next of kin." The message creates urgency by claiming funds will be forfeited to the government treasury unless claimed immediately.
Red flags:
- Unsolicited inheritances from unknown benefactors
- Private email addresses (jerrysmith@aol.com) instead of official bank domains
- Requests for personal banking details and upfront processing fees
- Emotional appeals referencing international conflicts and tragedy
14. Sophisticated settlement scam

Sophisticated settlement scams use professional property agent branding to request large sums of money. In this Australian example, the scammer demands an urgent $80,500 deposit transfer to a "Trust Account."
The email appears to come from a legitimate conveyancer with authentic formatting and specific BSB/account details. It creates artificial urgency with a deadline of "by 5 April at 5:00pm," and warns that "failure to provide will result in forfeiture of contract."
Red flags:
- Unexpected requests for early settlement transfers
- Urgent deadlines with contract forfeiture threats
- Generic sender details despite claiming to be from established firm
- Bank details provided via email rather than secure document portal
15. Deepfake impersonation with AI-generated documents
Deepfake impersonation scams use AI-generated video to pose as property sellers during verification calls, supported by fake documents such as driver's licenses, utility bills, and property records.
The fraudsters create real-time video interactions that respond to verification questions while presenting authentic-looking supporting documentation. The technology exploits traditional verification methods by making visual and audio confirmation unreliable.
Red flags:
- Video calls from unfamiliar devices or locations despite local seller claims
- Supporting documents that look perfect but fail database verification
- Reluctance to meet in person or provide additional verification methods
- Communication patterns that don't match previous interactions with the seller
Stay vigilant: Scammers are creative with phishing email attempts
AI-powered fraud eliminates the traditional warning signs, like poor grammar and obvious formatting errors. With these cues gone, the stakes are higher for industries like real estate, where clients now demand stronger protection.
Our data shows 79% of consumers are willing to pay more for secure real estate services. This proves that preventing wire fraud is now both a necessity and a competitive advantage.
The next step is clear: Remove email from money movement entirely. In an industry where mistakes cost hundreds of thousands, you can't afford anything less than full protection.
FAQ
Co-founder & CEO
Tyler brings a decade of leadership experience developing and launching technology businesses. Before co-founding CertifID, Tyler led new product development at BCG Digital Ventures for Mercedes-Benz, First American Financial, Boston Scientific, and Aflac.
Phishing remains the #1 entry point for real estate wire fraud. According to CertifID's 2025 State of Wire Fraud report, nearly $500 million in annual losses stem from business email compromise attacks targeting the real estate industry.
This article examines 15 real phishing examples, reveals the red flags you must recognize, and demonstrates how removing email from money movement becomes the only reliable defense against increasingly clever attackers.
What is a phishing email?
Phishing emails are fraudulent messages designed to impersonate trusted parties and manipulate recipients into revealing sensitive information or authorizing financial transactions.
In real estate, attackers commonly pose as lenders, underwriters, sellers, or even your own clients to redirect funds or capture wire instructions.
Consider a typical mortgage payoff fraud: You receive what appears to be a legitimate email from Mr. Cooper, complete with proper branding and formatting, requesting updated payoff information for a closing scheduled tomorrow.
The sender's address looks authentic, the urgency feels reasonable, and the request seems routine—until you discover that $275,000 has been wired to a fraudulent account.
These attacks work because they prey on the trust and time pressure built into real estate transactions.
If this feels uncomfortably plausible, you’re right. In the video below, CertifID’s Tom Cronkright and Kimberly Casanova show how fraudsters use ‘routine’ callbacks in real payoff fraud and what to do instead.
How phishing emails work (and why they bypass gut checks)
Phishing attacks succeed through social engineering—the psychological manipulation of human trust and decision-making under pressure. Fraudsters understand that title professionals work in high-stress environments where quick responses often keep a closing on track.
The mechanics involve techniques like:
- Compromised email accounts that provide authentic communication histories,
- Lookalike domains that differ by a single character
- Carefully researched transaction details gathered from public records.
Modern attackers use AI to study email patterns and generate messages that look and read like the real thing.
The problem with manual verification becomes clear during peak closing periods. When your team processes hundreds of files monthly, the callback-and-verify approach breaks down.
Checking emails on mobile devices after hours, pressure to respond quickly to "urgent" requests, and sheer volume make it easier for sophisticated fakes to slip through.
Types of phishing emails include:
- Classic phishing: mass emails with generic language and low-quality branding
- Spear phishing: highly targeted emails with personal details or transaction information
- Business email compromise (BEC): attackers impersonate trusted contacts by compromising real accounts
- CEO fraud: scammers pose as executives pressuring urgent actions (often leading to business email compromise)
- Brand impersonation: fake messages mimicking PayPal, Microsoft, Google, or DocuSign
- Government/tax scams — fraudulent IRS or regulatory messages demanding payments
- Smishing and vishing: phishing by text or phone call instead of email
Why real estate is a prime target
Real estate has a perfect storm for fraud: large transaction amounts, multiple parties communicating across fragmented systems, and historically low cybersecurity infrastructure.
With the U.S. median home sale price in Q2 2025 reaching $410,800, each successful attack yields hundreds of thousands of dollars.

The industry's vulnerability stems from its decentralized nature. Unlike banking, which invested heavily in cybersecurity following decades of attacks, real estate relies on thousands of independent title companies and law firms with varying security sophistication. State-by-state regulation creates inconsistent standards.
Title companies and closing attorneys still rely on email for critical tasks like verifying mortgage payoffs, confirming seller identities, and sending buyer wire instructions.
Attorneys and clients keep using email because it feels familiar, but that dependence gives fraudsters more chances to slip in and divert funds.

CertifID's analysis shows that once a company experiences a single high-risk transaction flag, the rate of suspicious activity increases up to 6x compared to peer firms. This suggests organized criminal groups systematically target specific businesses, hoping to exploit process gaps during busy closings.
Why email-dependent wire verification puts your business at risk
Every inbox functions as an unregulated payment rail, capable of authorizing hundreds of thousands of dollars in wire transfers without meaningful verification. Unlike banking systems with multi-factor authentication and fraud monitoring, email offers no safeguards to verify senders or wire instructions.
A single successful attack can wipe out your annual technology budget and threaten your business's survival. Traditional insurance policies often exclude wire fraud losses, leaving you personally liable for client funds.
The regulatory landscape adds another risk layer. As wire fraud incidents increase, state bar associations and insurance carriers scrutinize firms' cybersecurity practices more closely, potentially imposing higher premiums, coverage exclusions, or regulatory sanctions.
Phishing email examples
1. Dropbox phishing email example

Document-sharing platforms like Dropbox, Google Docs, and DocuSign are common targets in real estate transactions. These phishing emails are sent from generic-sounding names or compromised accounts of people you know. If a contact’s account was hacked, their email list can be used to spread the scam.
Clicking the link takes you to a fake login page that captures credentials while appearing nearly identical to the real Dropbox interface.
Red flags:
- URL contains "dropbox" but isn't a Dropbox domain
- Login page offers multiple email provider options
- Error message claims "Dropbox is having difficulties" before redirecting to the real site
2. Google Docs phishing email example

Like the Dropbox scam, this one starts with an email supposedly from someone you know.
Unlike the Dropbox scam, however, clicking on the link takes you to a real Google Docs page, and asks the user to grant permission to a third-party application entitled “Google Docs,” despite the fact it is not associated with the platform
Google has since added stricter rules for third-party apps, including restrictions on what names they can use.
If you grant access, fraudsters can use your login credentials to obtain your personal information, including your contacts list, to spread the attack.
Red flags:
- Hard to spot, but if you click the developer information, you can see it is not from the user you thought it was, after all
3. DocuSign phishing email example

The DocuSign phishing email mimics the company’s document completion notifications. They often claim "Your document has been completed" and use authentic branding, logos, and the familar blue color scheme.
The email comes from a suspicious sender address, and clicking the "VIEW COMPLETED DOCUMENTS" button redirects you to a malicious domain instead of DocuSign's official servers.
The attack works because people trust DocuSign notifications, particularly in real estate transactions where document signing is routine.
Legitimate DocuSign emails always include a 32-character security code in the "Alternate Signing Method" section. Phishing emails leave this out.
Red flags:
- Missing security access code in the alternate signing method section
- "View Completed Documents" button links to external, non-DocuSign domain
- Sender domain contains extra characters ("net001") not used by legitimate DocuSign emails
4. Bank of America phishing email example

A Bank of America phishing email uses authentic branding to claim an account has been suspended due to "unusual activity detected."
The email creates urgency by threatening account limitations unless the recipient downloads an HTML attachment for "verification." The message looks professional with clean formatting, footer disclaimers, and contact details that appear legitimate.
However, legitimate banks never ask customers to download attachments to verify their accounts. The email uses a generic greeting like "Valued Customer" and try to pressure the reader with threats debit or credit card limitations.
The email’s polished appearance makes it harder to detect, especially for title professionals juggling multiple business banking relationships.
Red flags:
- HTML attachment required for "verification"
- Generic greeting "Valued Customer" instead of account holder's name
- Urgent threats of account limitations to pressure immediate action
- Requests to download files rather than directing to official bank portals
5. Wells Fargo phishing email example

Wells Fargo phishing emails mimic the bank’s red and yellow branding and warn that an account has been locked pending verification. The email claims purchases and balance transfers will be declined, creating urgency around frozen access.
It directs recipients to what looks like the correct URL to unlock their account. The email’s professional formatting makes the request appear credible.
However, the sender domain differs from Wells Fargo’s official wellsfargo.com; in this case it’s noreply@weiis-mail.com. Phishing domains commonly add hyphens, swap letters, or insert extra words to mimic a real address.
These tactics can bypass email security filters and exploit recipients’ unfamiliarity with text-based phishing. Wells Online is also not a legitimate name used by Wells Fargo.
Red flags:
- Sender domain "weiis-mail.com" instead of official "wellsfargo.com"
- Urgent account lockdown claims designed to provoke immediate action
- Generic verification URL that doesn't match legitimate Wells Fargo domains
- Unsolicited account status notifications
6. PayPal phishing email example

This PayPal phishing example uses the company’s blue branding to announce that an unexpected $479.35 charge will be deducted from the recipient's account.
The email creates panic by claiming unauthorized charges while providing a toll-free support number for "cancellation." It includes convincing details like invoice numbers and dates.
However, the message uses generic salutation "Dear Customer" and asks you to call a phone number rather than directing users to PayPal's official website, which legitimate PayPal notifications always do.
Red flags:
- Grammatical errors like "will be going to be deducted”
- Unexpected charge notifications for services you didn't purchase
- Generic greeting "Dear Customer" instead of account holder's name
- Phone number provided for dispute resolution instead of website links
- Urgent 24-hour deadline designed to provoke panic response
7. Email providers phishing example
The same tactics used in document and bank phishing can also target your email credentials, which can give scammers access to the person’s contacts—and, potentially, their banking, shopping, or social media accounts.
Various forms of “validate your account” Gmail messages have made their rounds, telling users to verify their information to avoid account suspension.
They are taken to a real-looking log-in screen, and scammers use their information to access, among other things, the user’s contact list and spread malware or more validation emails.
Users should take note of the URL—which is not actually a Google one—and the fact that, once they’ve entered their email address, their profile picture does not appear before they’re asked for their password.

Email provider phishing scams are especially troubling for real estate agents. Many agents still use personal Google email accounts to communicate with clients, even though experts and brokerages advise against it.
A scammer can simply find their email on a real estate site, Facebook, or LinkedIn, and tailor an attack based on that information. From there, they can steal client details and possibly trick them into sending money or banking credentials, all while pretending to be the agent.
8. Real estate phishing email example

A recent Zillow-based scam was sent to real estate agents, complete with authentic-looking logos, and congratulated the user on their new leads from ZillowAds, which had to be “unlocked” with their contact details and a fee of $5.00.
At least one agent was tricked into providing their credit card information, and missed the only potentially obvious red flag: the fact the domain name was “Zillow.pro” instead of a .com address.
9. Virus and malware phishing example
Virus and malware attacks appear to come from an internal administrator sending an "Important - Internal ONLY" message with a ZIP file attachment (e.g., internal_04531572.zip).
The email is professionally formatted with confidentiality notices, legal copyright information, and detailed file validity data to appear legitimate. The extensive boilerplate text about intellectual property rights and legal consequences creates an illusion of authenticity.

However, the ZIP attachment contains malware that encrypts across your computer once downloaded. The sender's domain, "tomokuhus.se," doesn't match typical internal company addresses, and legitimate internal communications rarely require downloading compressed files for routine business.
10. Facebook phishing email example

This Facebook phishing email mimics the platform’s branding, uses a personalized greeting "Hi Paulo.", This may come from a look-alike address such as "security@facebookmail.com" and include a reset code (66631625) and "Change password" button to complete the illusion.
Red flags:
- Sender domain "facebookmail.com" instead of official "facebook.com"
- Unsolicited password reset requests you didn't initiate
- Direct reset codes provided in email rather than secure website prompts
- Professional appearance designed to bypass suspicion during mobile viewing
11. Xfinity phishing email example

Attackers send users an email with the Xfinity logo and layout. This message claims to be a confirmation to verify you’ve authorized a payment on a credit card.
Since it’s a fake number, it confuses the target and entices them to click on the “Comcast Billing Invoice” link in the hopes of understanding or fixing the error.
This link leads to a fake domain that prompts the user to download a .php file they believe to be the invoice. Instead, it contains a virus that infects your computer. This malware can compromise secure information stored therein.
Red flags:
- Does not use the customer's name or account number
- Link in the email. Genuine providers direct customers to the company’s official website, which always requires logging in
12. Amazon phishing email example

Amazon phishing emails like this use Amazon's branding and warn, "We have locked your Amazon account and all pending orders," citing billing information mismatches. The email creates urgency by threatening order cancellation within 3 days unless the recipient clicks "Check Now" to verify billing details.
Red flags:
- Displays as mailing list rather than official Amazon communication
- Generic greeting "Greetings from Amazon" instead of account holder's name
- Urgent 3-day deadline designed to provoke immediate panic
- Requests verification through external "Check Now" button
13. Inheritance scam email example

This inheritance scam email uses formal letterhead formatting to announce a £32 million inheritance opportunity from a deceased Libyan national.
The scammer poses as "Mr. Jerry Smith," a bank auditor who discovered an abandoned account, offering 35% of funds in exchange for serving as "next of kin." The message creates urgency by claiming funds will be forfeited to the government treasury unless claimed immediately.
Red flags:
- Unsolicited inheritances from unknown benefactors
- Private email addresses (jerrysmith@aol.com) instead of official bank domains
- Requests for personal banking details and upfront processing fees
- Emotional appeals referencing international conflicts and tragedy
14. Sophisticated settlement scam

Sophisticated settlement scams use professional property agent branding to request large sums of money. In this Australian example, the scammer demands an urgent $80,500 deposit transfer to a "Trust Account."
The email appears to come from a legitimate conveyancer with authentic formatting and specific BSB/account details. It creates artificial urgency with a deadline of "by 5 April at 5:00pm," and warns that "failure to provide will result in forfeiture of contract."
Red flags:
- Unexpected requests for early settlement transfers
- Urgent deadlines with contract forfeiture threats
- Generic sender details despite claiming to be from established firm
- Bank details provided via email rather than secure document portal
15. Deepfake impersonation with AI-generated documents
Deepfake impersonation scams use AI-generated video to pose as property sellers during verification calls, supported by fake documents such as driver's licenses, utility bills, and property records.
The fraudsters create real-time video interactions that respond to verification questions while presenting authentic-looking supporting documentation. The technology exploits traditional verification methods by making visual and audio confirmation unreliable.
Red flags:
- Video calls from unfamiliar devices or locations despite local seller claims
- Supporting documents that look perfect but fail database verification
- Reluctance to meet in person or provide additional verification methods
- Communication patterns that don't match previous interactions with the seller
Stay vigilant: Scammers are creative with phishing email attempts
AI-powered fraud eliminates the traditional warning signs, like poor grammar and obvious formatting errors. With these cues gone, the stakes are higher for industries like real estate, where clients now demand stronger protection.
Our data shows 79% of consumers are willing to pay more for secure real estate services. This proves that preventing wire fraud is now both a necessity and a competitive advantage.
The next step is clear: Remove email from money movement entirely. In an industry where mistakes cost hundreds of thousands, you can't afford anything less than full protection.

Co-founder & CEO
Tyler brings a decade of leadership experience developing and launching technology businesses. Before co-founding CertifID, Tyler led new product development at BCG Digital Ventures for Mercedes-Benz, First American Financial, Boston Scientific, and Aflac.
Sign up for The Wire to join the conversation.





.png)



